
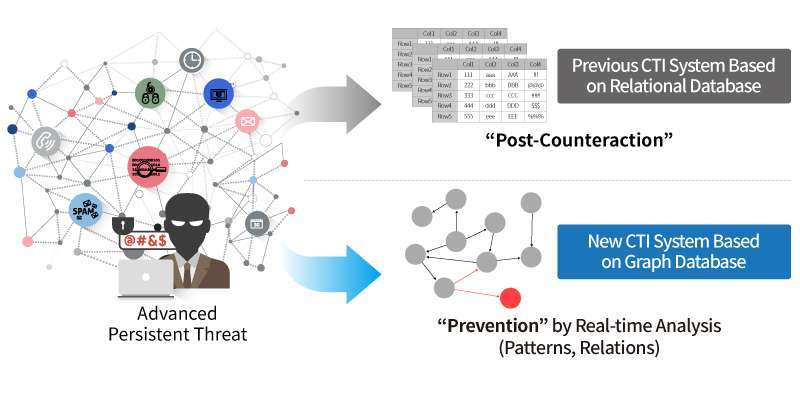
How a Graph DBMS Enhanced the Cyber Threat Intelligence of Government Agency | by Joe Suh | AgensGraph | Medium
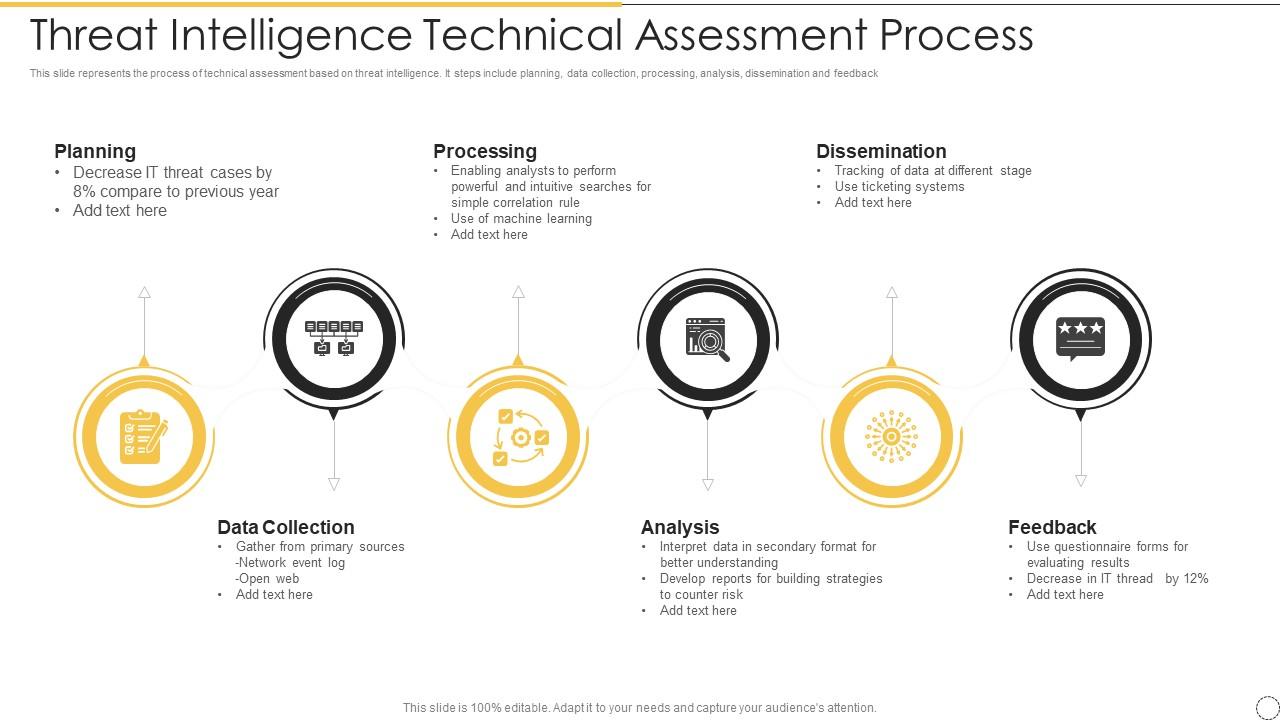
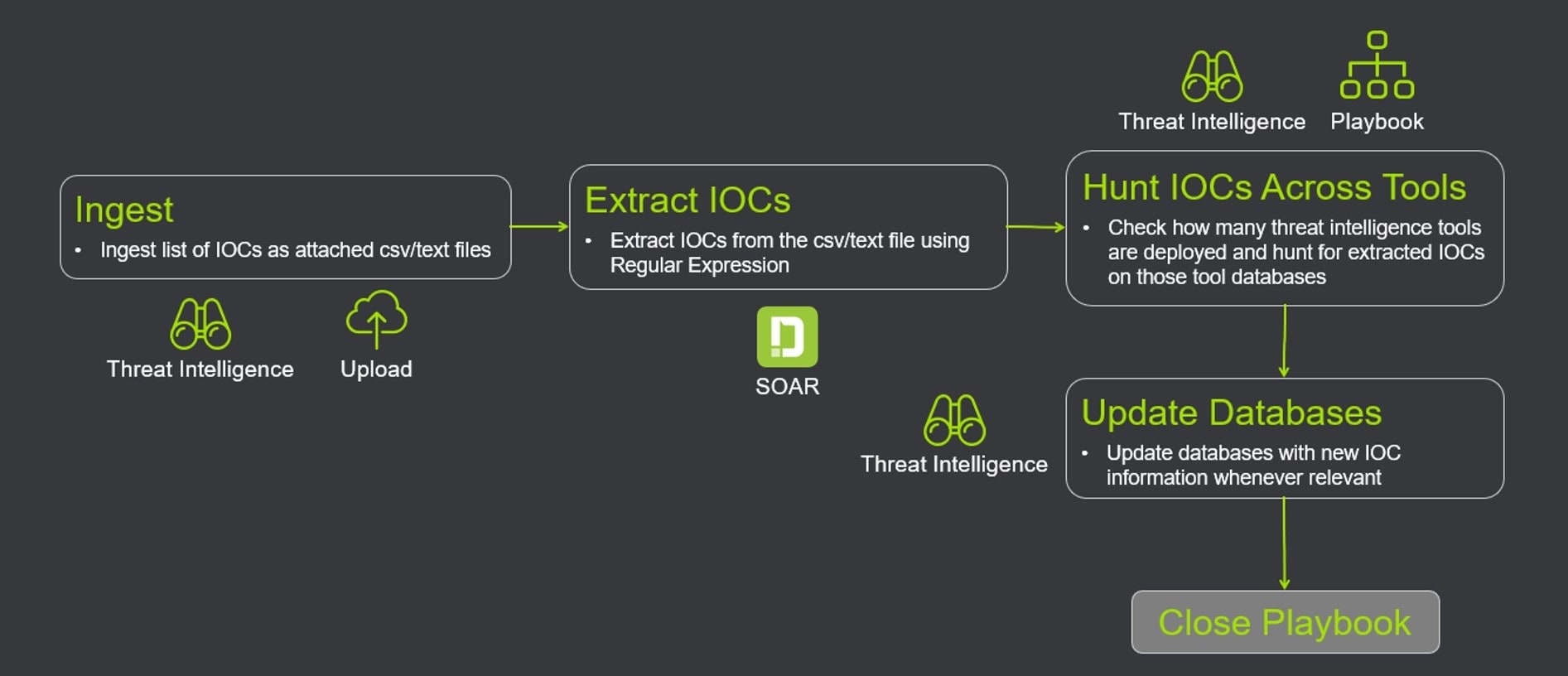
Threat Intelligence Technical Assessment Process | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

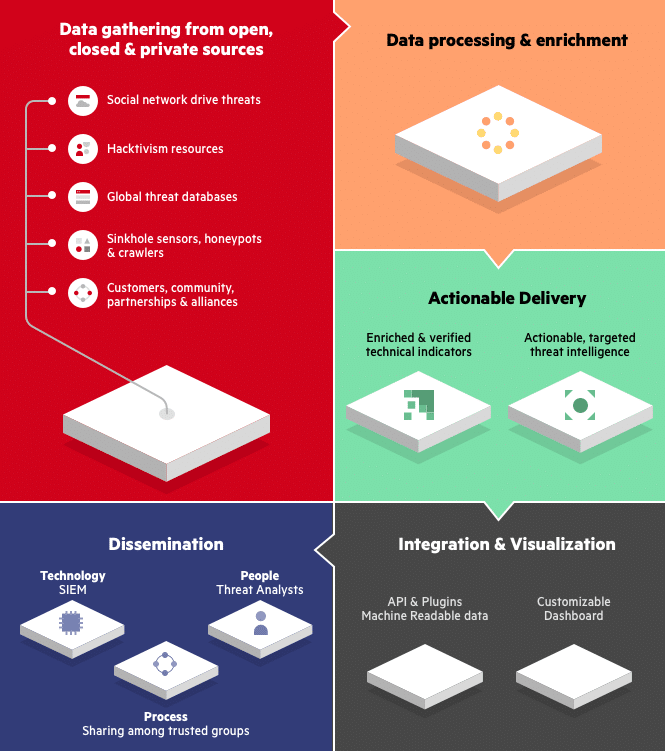
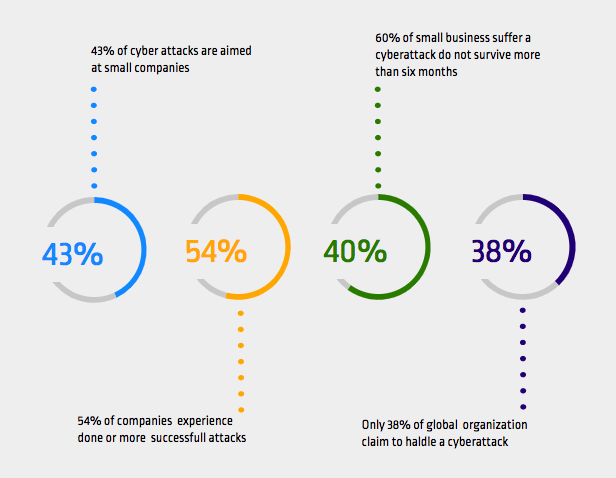
What Is Cyber Threat Intelligence? Definition, Objectives, Challenges, and Best Practices - Spiceworks

Deep Inside Cyber Threat Intelligence: Make Informed Decisions About Your Security | by Md Asif | Analytics Vidhya | Medium

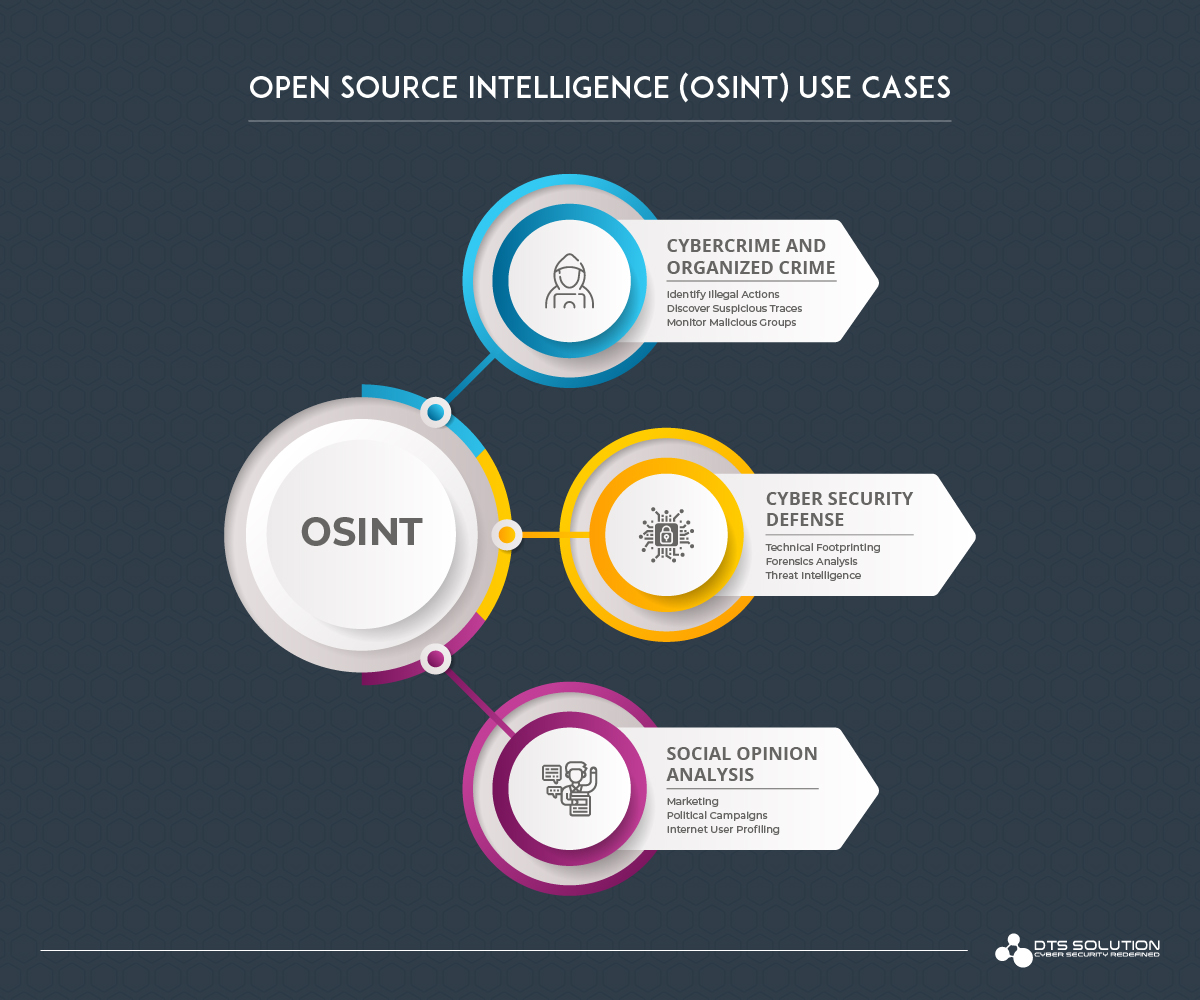
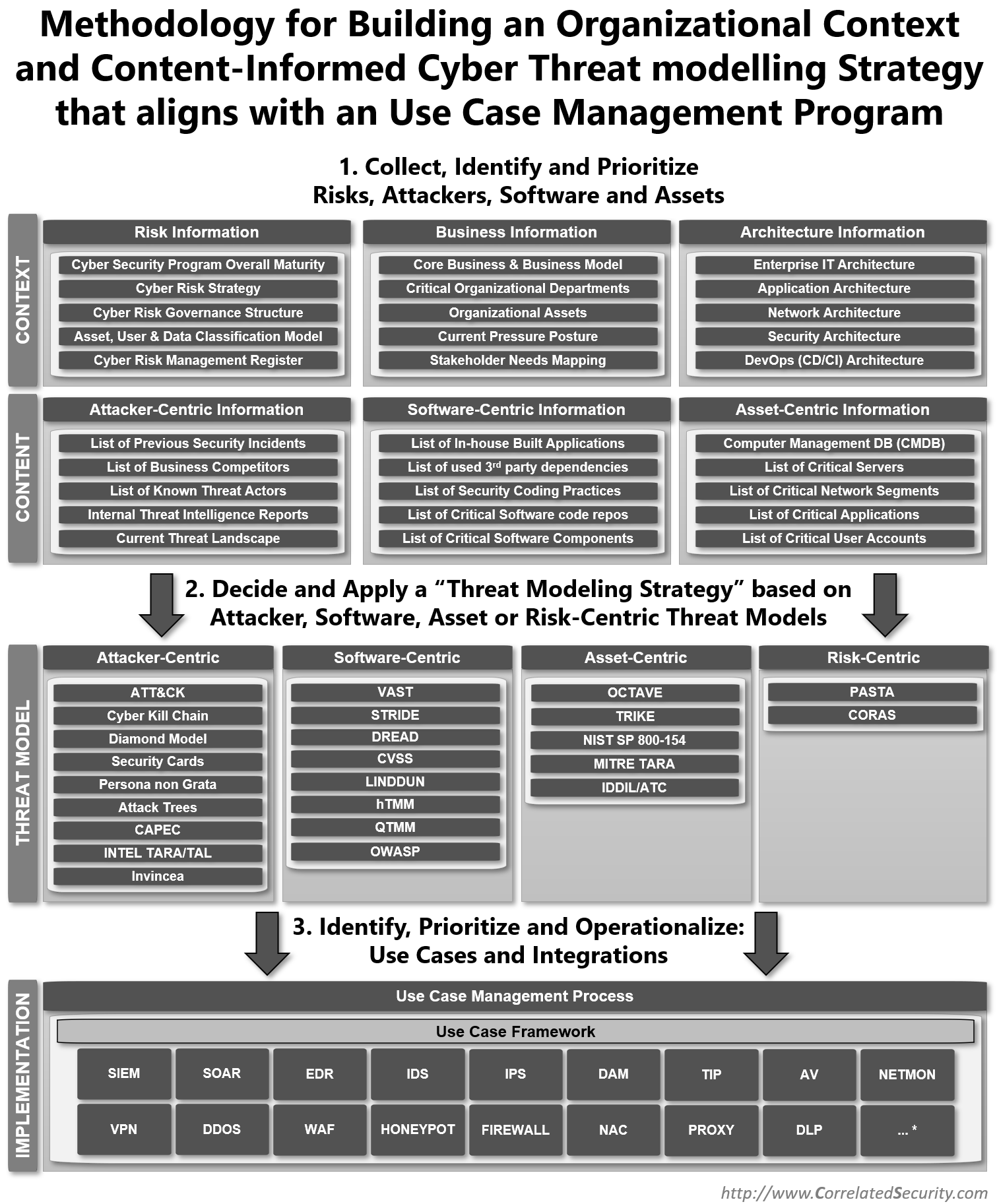







![What is Cyber Threat Intelligence? [Beginner's Guide] What is Cyber Threat Intelligence? [Beginner's Guide]](https://www.crowdstrike.com/wp-content/uploads/2019/07/crowdstrike-threat-intelligence-areas.png)
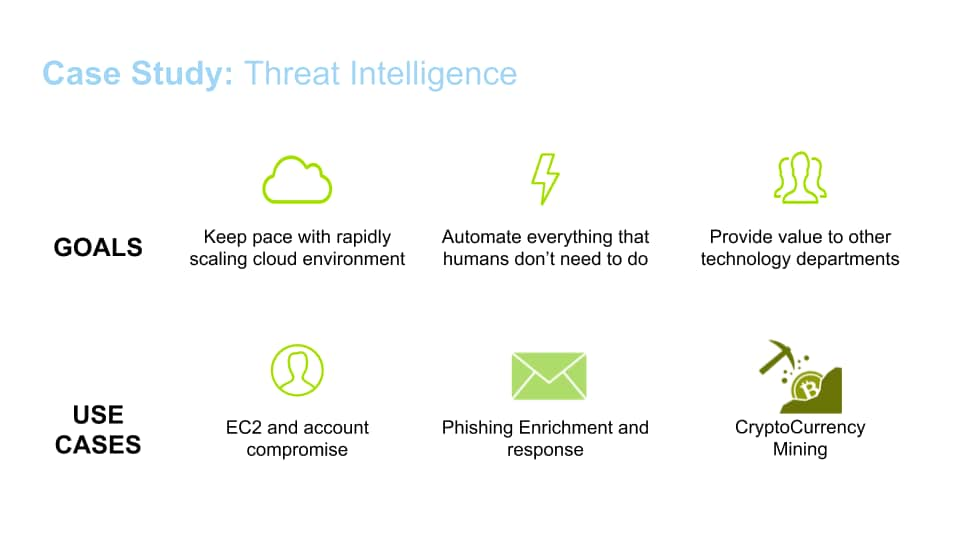

![What is Cyber Threat Intelligence? [Beginner's Guide] What is Cyber Threat Intelligence? [Beginner's Guide]](https://www.crowdstrike.com/wp-content/uploads/2019/07/threat-intellgence-use-cases-types-1024x583.png)
